Innovative Cybersecurity and Data Protection Practices for the Digitally Driven World

Image via rawpixel (copyright-free)
Rapid growth and innovation in technology have enabled humans to solve many challenging problems. With faster, cheaper, and effective technological solutions, we have entered the Information Age where data serves as fuel. Unlike other sources of fuel, data is not limited. It is created every second by everyone at an unimaginable rate. A recent study shows we generate 2.5 quintillion bytes of data every day. [1] This number is only going to increase with increasing dependency of organizations and governments upon IoT devices, digital tools, and services to drive the economy and fulfill the needs of society.
WHY CYBERSECURITY?
With more data, comes more risk. If the private and confidential data of the public goes in the wrong hands, it can lead to severe damage to corporations and individuals, and hence needs to be protected.
Statistics show that there is a web attack every 39 seconds across the globe [2] and 30,000 new websites get hacked every day on average. [3] Globalization has surely facilitated trade and sharing of ideas, but it has also made the whole world one entity, making them dependent on each other and hence vulnerable.

Image via rawpixel (copyright-free)
In the middle of a global pandemic COVID-19, our dependence on cyberspace has grown more than ever. From basic transactions to government bodies’ meetings, everything is being done online. As online activities increase, so does the risk of cyber-attacks. We have started to realize that the protection of our data is as important as the proper utilization of it.
Murphy’s law holds true in cyberspace which states, “If anything can go wrong, it will go wrong.” meaning, even a single mistake can lead to disruption of organizations and even governments.
WHAT ARE WE DOING RIGHT?
Many organizations already have good security policies in place with a dedicated department for security to safeguard users’ data. The security teams identify and mitigate threats that can potentially harm a company. Apart from that, companies are also following different tactics to ensure data security, such as penetration testing, vulnerability management, endpoint security, etc.

Image via rawpixel (copyright-free)
Developers have started adopting necessary security measures like 2-Factor Authentication, web-application firewalls on both client as well as server sides, etc In recent years many companies have come up with ‘Responsible Disclosures Programs’ persuading good minds to hack for good. Platforms like HackerOne and BugCrowd, facilitate such programs and award white hat hackers with monetary rewards, popularly known by the buzz word ‘bug bounty’ for finding vulnerabilities in their companies and reporting them ethically.
IS IT (IN)SUFFICIENT?

Image via rawpixel (copyright-free)
Still, a huge number of companies don’t have adequate security measures due to various reasons, which puts users’ data at risk. A recent study by Acunetix shows that 46% of web applications suffer from critical vulnerabilities and 87% suffer from medium-level vulnerabilities. [4] The following chart throws more light on this.
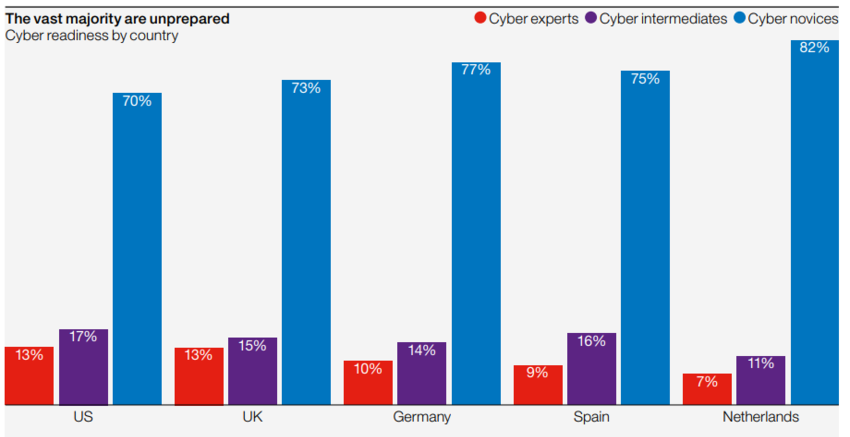
Source: Survey conducted by Forrester Consulting on behalf of Hiscox
Less secure systems lead to massive data breaches , which have become a very common incident in recent times. [5] This leads to leakage and misuse of users’ private and confidential data ranging from their contact details to credit card information.
Popular bug-bounty platforms fail to ensure 100% security as most companies allow only a limited portion of their assets to be tested by ethical security researchers, giving cybercriminals ample space to hack on. Some companies are also reported to give very little monetary rewards as compared to the potential loss in certain cases, [6] which pushes white hat hackers to the black side.
FUTURE CHALLENGES
100% security is a myth
Companies always go through changes. Applications always roll out updates. Technologies change all the time. Today’s security can be tomorrow’s vulnerability.
If all goes right, we have humans as masters, who are one of the most vulnerable pieces in a system. No matter how secure the application is, it can be hacked in minutes if the administrator’s password is ‘password’.
New technologies can not only introduce new vulnerabilities but can also turn old weaknesses into potential vulnerabilities. PTSecurity reported, web-applications with “extremely poor” security have doubled compared to the previous year [4] .

Image via rawpixel (copyright-free)
Over time, vulnerabilities might have remained the same, but the potential loss has increased many folds. The number of cases of ransomware attacks, data breaches, etc has increased globally, which demands new innovative solutions instead of the traditional approach.
Research in quantum computing may facilitate cyber-attacks with exponentially faster computing power enabling hackers to destroy major encryptions and making security even more difficult.
Hence, to solve such problems which have never existed, we need solutions which never existed.
INNOVATIVE SOLUTIONS

Image via rawpixel (copyright-free)
1. HORIZONTAL VS. VERTICAL GROWTH
It’s not about Horizontal or Vertical, but Horizontal and Vertical.
Horizontal growth , i.e. expansion of existing security policies to every sector and organization is as important as Vertical growth , which means developing new policies and measures to protect user data in a more efficient way. Only with balanced growth in both the fields, can we hope for a more secure world.
2. PEOPLE ARE VULNERABILITIES
Every employee is a potential entry point to the internal network for an attacker. A simple social engineering trick can compromise an employee’s identity leading to a severe attack. Employees must be tested and trained regularly for such attacks.
Equality is not always good
Not every employee should be authorized to alter database entries. There must be a hierarchy in place giving different privileges to different people.
3. MONITORED UPDATES
A large number of companies have been compromised because of outdated software and services in place. An automated system should monitor all the assets owned by the company and update them as soon as a new patch is issued. 5G technology can aid to achieve the same globally, keeping all the systems updated across the globe all the time. This will remove many CVEs which are prime sources of cyber attacks.
4. WHITE-HAT VS. BLACK-HAT
Employees switch jobs for better recognition of their skills. If white-hats were paid more than black-hats, we’d have had fewer cybercriminals, if not zero.
The term “Ethical” in “Ethical hacker” forces us to think a hacker by default is unethical, which is not the case. The incentives and rewards which hackers see appear huge to them as compared to the risk involved, which persuades good minds to do evil.
Black-hat hackers enjoy full freedom while white-hat hackers are restricted to certain areas for testing. An army can’t save a country if soldiers are confined to bunkers and criminals are free to attack from wherever they want. Providing ethical researchers more freedom and access to resources will not only make security easier but also transform black-hats into white-hats.
5. STRICTER LAWS AND RULES
Governments must make and implement stricter rules for cybersecurity, and keep organizations in check.
- Companies with more than a certain user base must meet predefined security criteria.
- Startups must have a security team from the very start.
- Cyber-police should keep people in check and make them follow government rules.
- Cyber rules should be an integral part of the school’s curriculum same as the “Fundamental Rules”.
6. AHEAD OF “THEM”
Since 100% security is impossible, we need to be ahead of the criminals in order to stay safe.
More research in cybersecurity should be promoted and facilitated by increasing funding. Cybersecurity should be considered as important as a country’s army because weapons can’t help if they are open to cyber attacks.
There have been cases where claims have been made to have successfully compromised fingerprint scanners as well. [7] This shows we need better scanning technology, encryptions , and cryptography in the future.
7. BLOCKCHAIN TECHNOLOGY
Arguably claimed by some experts, Blockchain can be the future of the internet. Well, it may not be the case, but it can surely help make cloud services more secure.

Image via rawpixel (copyright-free)
In blockchain technology, a digital ledger is maintained where the information is added permanently after verification. With more transparency and visibility to individuals, it makes tampering of data difficult. Further research in blockchain technology is needed for cloud protection as almost 95% of companies rely on cloud services. [8]
FINAL WORDS
To keep the cyber-threats in check, cybersecurity researchers need to keep on finding innovative technological solutions. By Implementation of better security policies and measures, a safer world will not just remain a dream.
REFERENCES
- How Much Data Do We Create Every Day? The Mind-Blowing Stats Everyone Should Read by Bernard Marr, Forbes, Published on May 21, 2018
- Hackers Attack Every 39 Seconds - Security Magazine, studied at University of Maryland, Published in Security Magazine on February 10, 2017
- 30,000 Web Sites Hacked A Day - Forbes by James Lyne, Forbes, Published on Sep 6, 2013
- Acunetix’s report “Web Application Vulnerability 2019”, Acunetix, Published on March 5, 2019
- The 15 biggest data breaches of the 21st century, by Dan Swinhoe, CSO, April 17, 2020
- #nofreebugs twitter hashtags by security researchers against their exploitation [started in 2011]
- Hackers Claim ‘Any’ Smartphone Fingerprint Lock Can Be Broken In 20 Minutes, by Davey Winder, Editors’ Pick, Forbes, Nov 2, 2019
- Changing Attitudes Towards Business Intelligence in the Cloud, DataSync, Published on August 16, 2017